Putting aside any political motivations behind these attacks, and looking at the embedded trojan from the technical point of view, a pretty interesting piece of code is revealed.
Being an executable embedded into Microsoft Word document, the trojan itself is a CDialog-based VC++ MFC application. When it starts, it checks if there is a driver installed in the system called tmpreflt.sys. This driver appears to belong to OfficeScan software product from Trend Micro. The trojan tweaks its logics depending on the presence of tmpreflt.sys and then installs a new driver resdr32.sys that it reads and decrypts from its own resource section. This driver has device name FILEGUARDDOS and it is presumably designed for self-protection purpose.
The payload code of the trojan is encrypted in its resource section. After it decrypts the code, it starts its own executable, allocates memory in the address space of its "cloned" process, writes there the newly decrypted payload code, and spawns an execution thread in it.
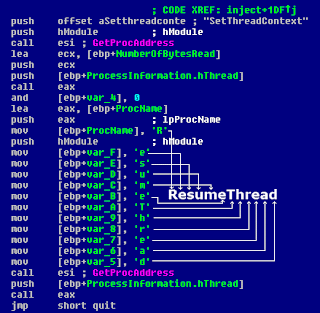
Once the second instance of the trojan is started and the injected payload code is activated, it will contact its command-and-control server mmwbzhij.meibu.com on ports 8585 and 8686.
The communication traffic is encrypted. The commands issued by the C&C server will instruct the trojan to download and run additional components. For example, the newly downloaded components can be created under the following filenames:
- C:\loader.exe
- C:\ml.exe
- %System%\EventSystem.dll
The trojan constantly submits POST requests to the remote host with the following format:
http://mmwbzhij.meibu.com:8686/[random characters].[random file extension]
where [random characters] string may look similar to:
- qRXycRXuwJ11749
- PqJNBkcPDm18630
- ZPDPyZkZcV23661
and [random file extension] can be any of the following: rm, mov, mp3, pdf.
One such POST request is shown below:
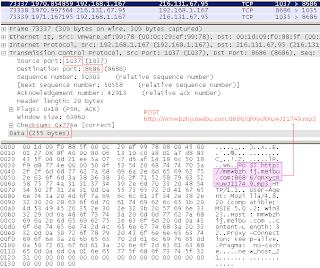
The purpose of these requests is not clear - the random characters contained in the POST request can potentially be used by the server to determine the encryption key that is different for every communication round (a hopping key).
To run every time Windows starts, the trojan drops its copy under a variable name, such as %System%\winpp.exe or %System%\instoll.exe and then registers its full path filename in the value:
"StubPath"
of the registry key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{345A814E-7F4F-1BCD-0104-050302030401}
Fully automated reports can be found here and here.
